Application Penetration Testing Services
Adhere to the latest compliance standards and fast track time to launch. Our CREST-approved application penetration testing services detect and nullify every possible vulnerability.
Surgical Penetration Testing
Our comprehensive penetration testing services cover vulnerabilities across applications of every shape and form
Web App Pentesting
Mobile App Pentesting
Thick Client Pentesting
On-Demand Pentesting
Fortify Your Application
Empower Your Application's Security. Experience measurable outcomes that elevate your application's security posture with our proven process.
Proven methodology
Get comprehensive insights from a tried and tested hybrid testing process
Ensure Data Security
Detect data leaks emerging from local storage issues
Strengthen Backend Tech
Ensure backend services and servers are robust and free from security flaws
Ensure App Resilience
Make your application resilient to reverse engineering
Fix Business Logic
Custom checklist created as per the business logic of the application
Identify Weak Algorithms
Identify weak algorithms and mitigate them to build a robust mobile application
Comprehensive Coverage With Every App Pentest
- API Security Assessment
- Secure Data Storage
- Auth & Authorization Assessment
- Security Config Review
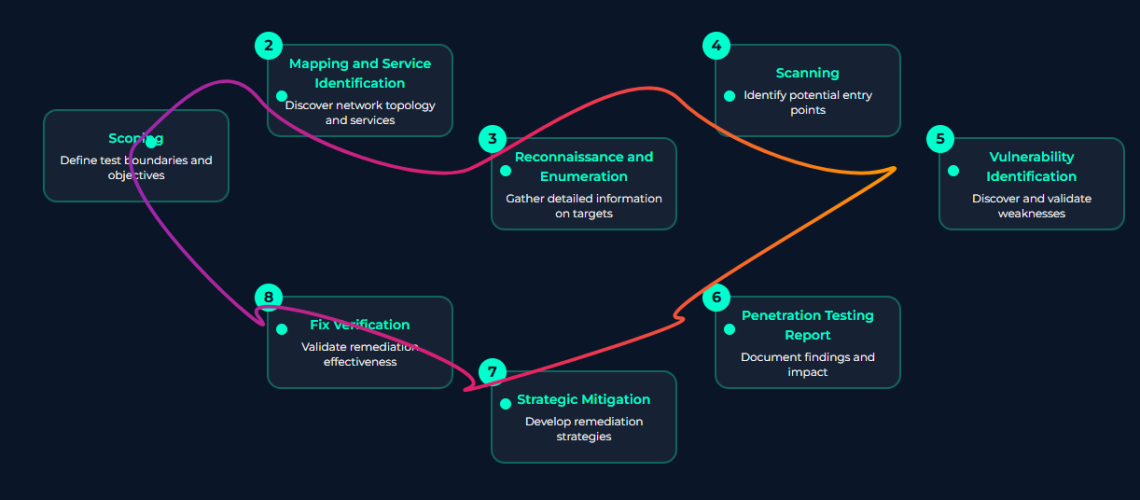
Application Penetration Testing process